|
Packet sniffer is more a troubleshooting tool than a specific tool for constant netflow monitoring.
Packet sniffer allows you to capture every packet and store it on your hard disk. Letís say you
want to do 24 hour monitoring - 7 days a week, this way you need an incredible big hard disk.
Caligare Flow Inspector netflow software collects statistics not the whole packet, which is why
this method is more suitable for constant monitoring and data analyzing.
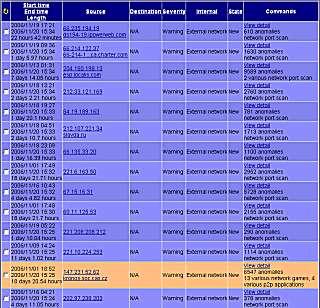
(click for enlarge)
Network port scanning
The network port scan module detects many suspicious activities as worms, BOTNET scanning attacks, etc.
The latest software version detects stations which are scanning the network and looking for network
vulnerabilities e.g.: Microsoft WINS, NETBIOS, Microsoft DS, SOCKS, Microsoft SQL, MySQL, web cache,
VNC, Microsoft EPMAP and Microsoft terminal services. This module also detects SWIFT, DABBER,
QWIN worms and many other unusual activities.
Host port scanning
This network detection module identifies attackers that scan TCP or UDP service ports for vulnerabilities.
This module supports only scanning of applications that uses low ports (1-1024).
ICMP flooding
The ICMP flooding detection checks how many ICMP packets the host is sending. If the number of packets
exceeds the configured threshold, then the system creates a new anomaly. System recognizes long ICMP
messages (>1000B) so that you can configure different thresholds for short ICMP messages and long
ICMP messages. Software is capable of detecting unreachable messages (often it signify infection by
worm) and other ICMP message types.
TCP/SYN flooding
The TCP/SYN flooding module detects direct or distributed flooding of network with TCP connection
requests. This attack is characteristic for distributed denial of service attacks.
Network games detection
The network games detection module uses heuristic methods to detect network games. Many games use the
same TCP or UDP port so it is very difficult to say which game was used. The latest version supports
the following games: Need for Speed, Diablo, Civilization, Worms 3D, Microsoft DirectX games, Railroad
Tycoon, Athena Sword, Unreal, Team Speak, Battlefield 1942, Battle Zone, Age of Empires, Heretic, Hexen,
Doom, Call Of Duty, Castle Wolfenstein, Battlefield 2142, MSN Game Zone, Alien vs. Predator, America's Army,
Battle.NET, Vietcong, Half-Life and Quake.
Peer to peer application detection
Peer to peer applications waste network bandwidth the most, so detection of these applications is very
useful for many administrators, detection of these applications is very, very difficult. Network analysis
software uses well-known TCP/UDP ports and some heuristic methods, but in some cases may detect false
positives. The latest version supports detection of the following applications: FastTrack, Kazza,
Overnet, Kademlia, Aimster, GNUtella, GNUtella2, WinMX, OpenNapster, Direct Connect, SoulSeek,
eDonkey and BitTorrent.
|



